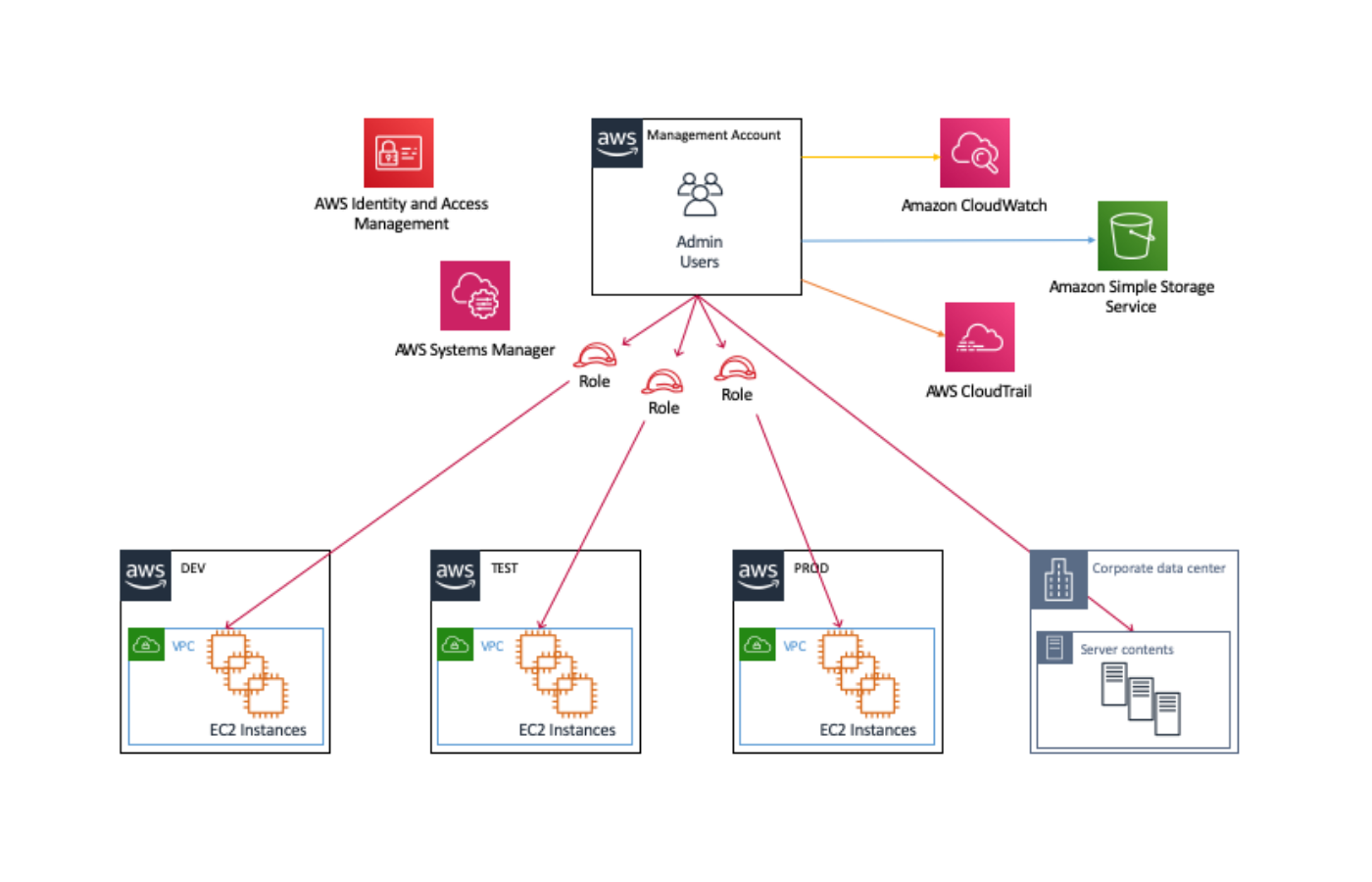
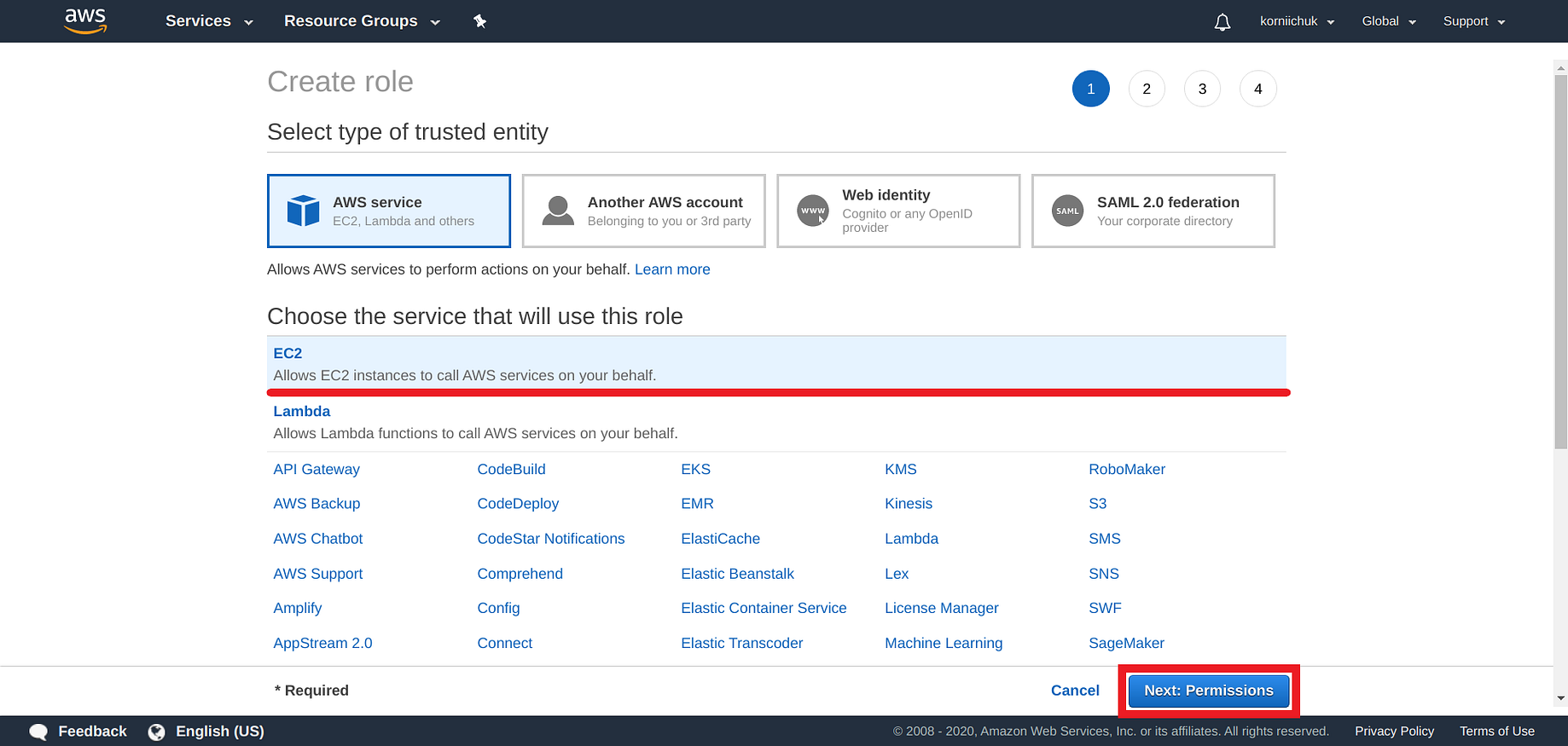
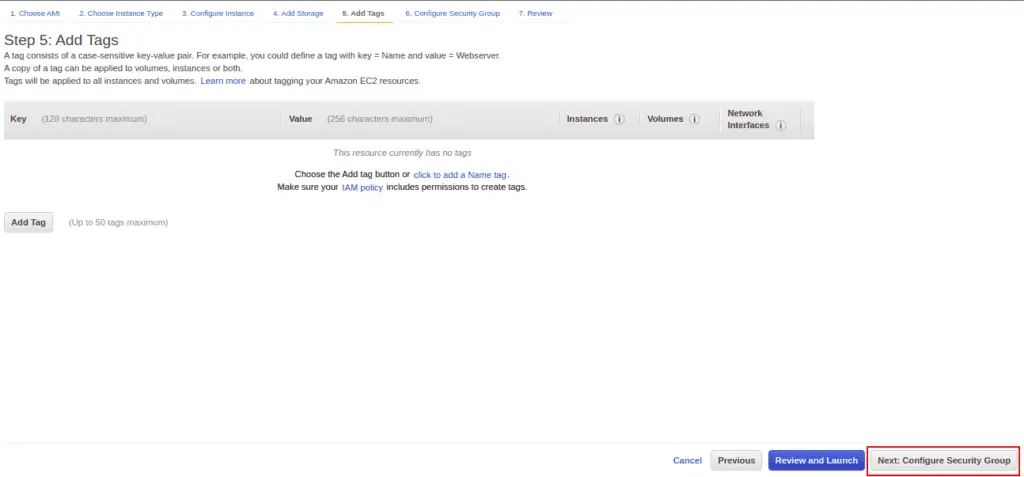
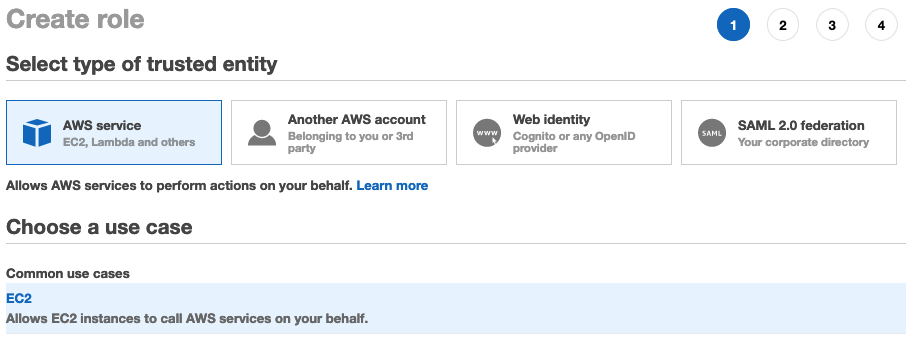
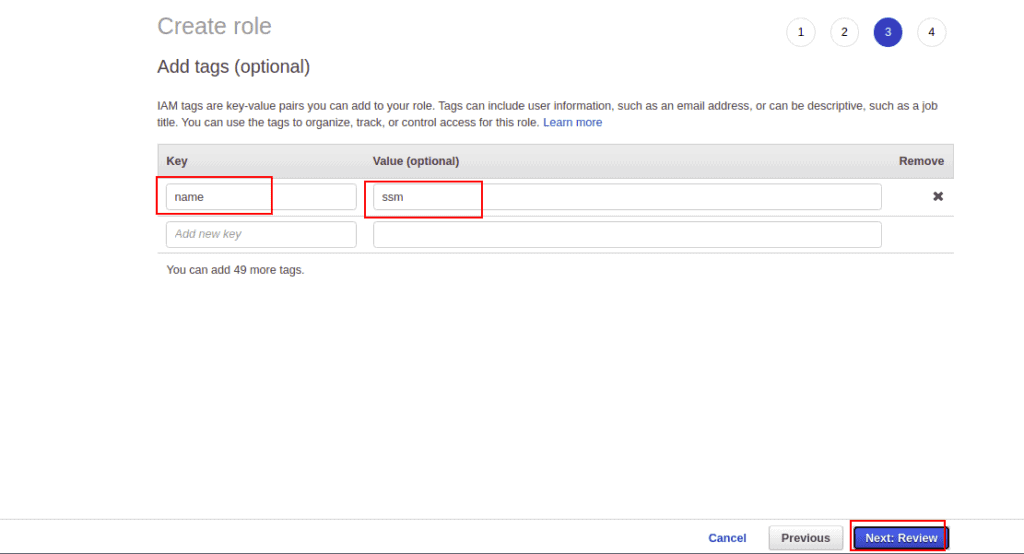
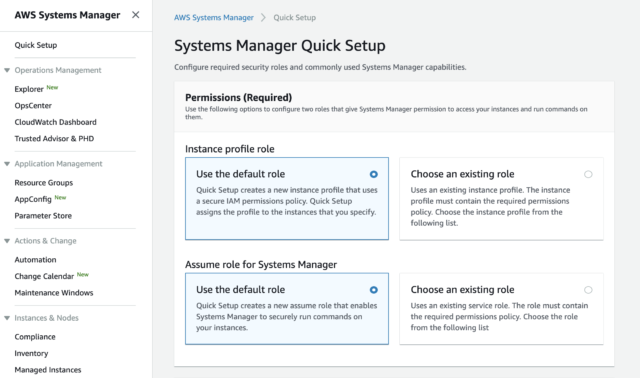
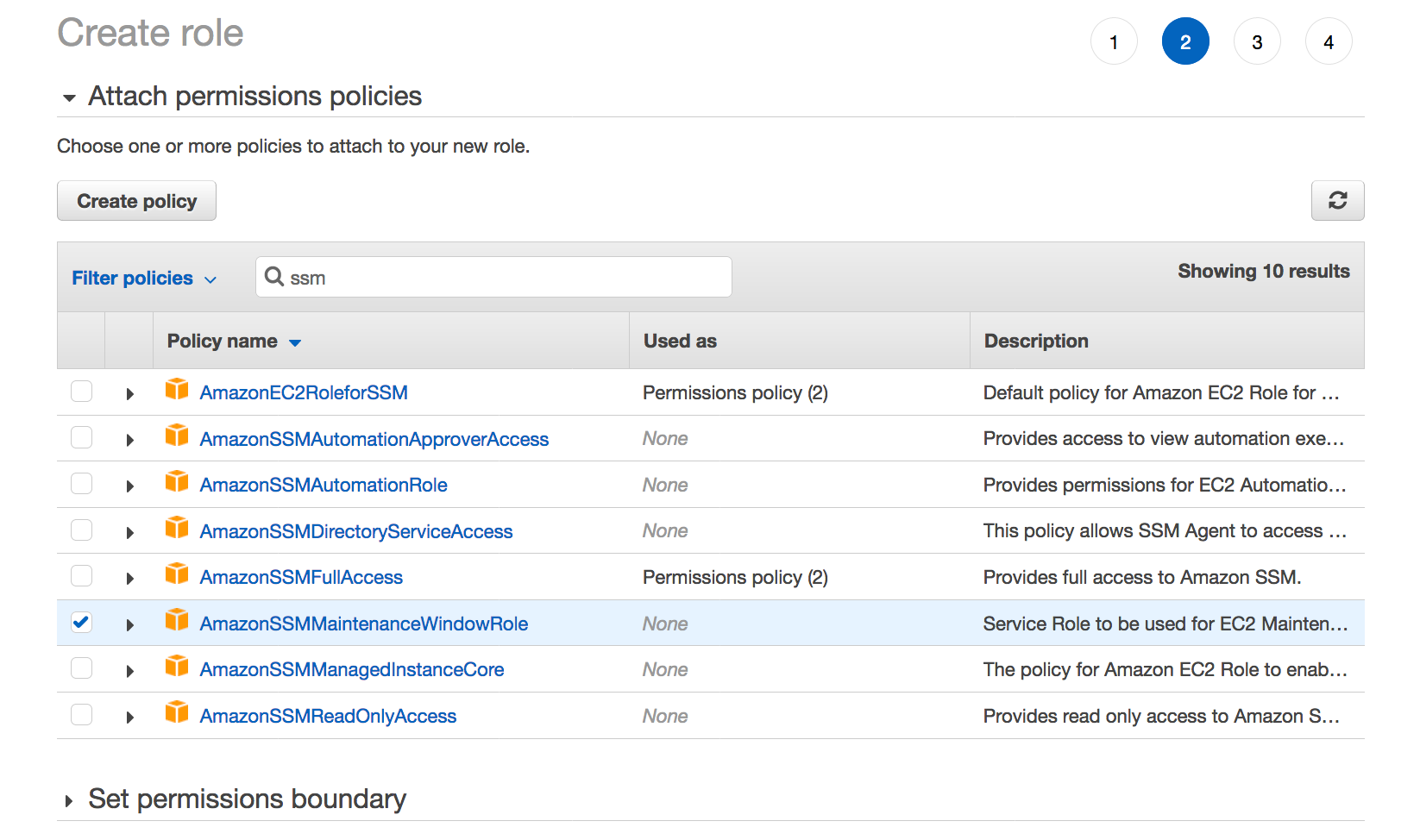
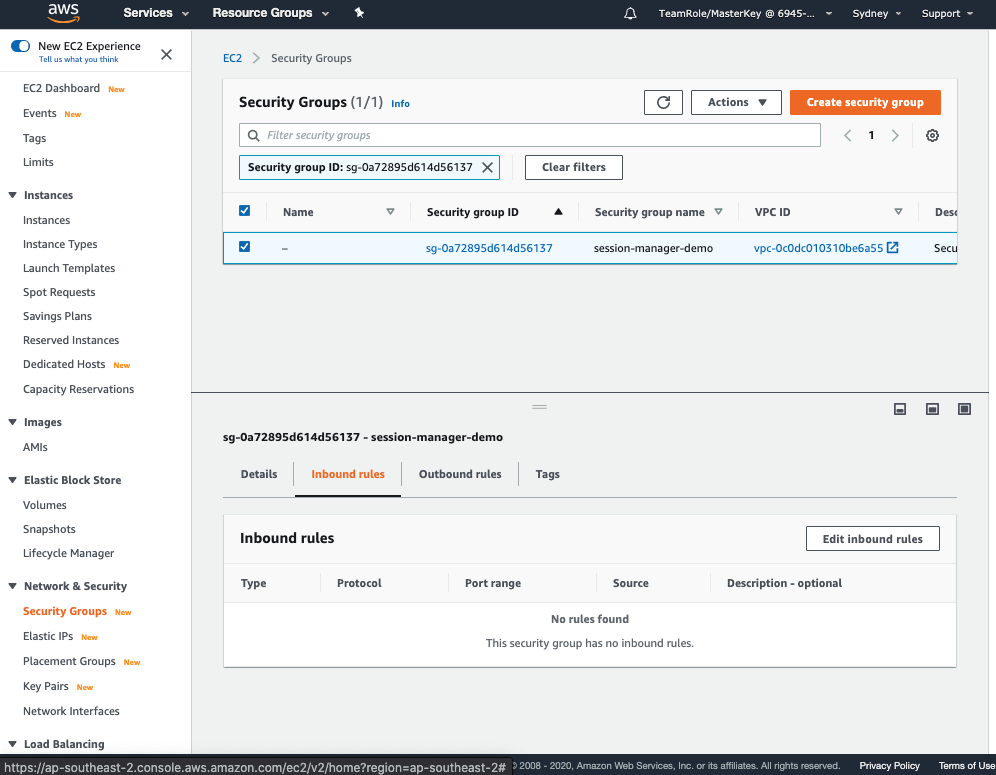
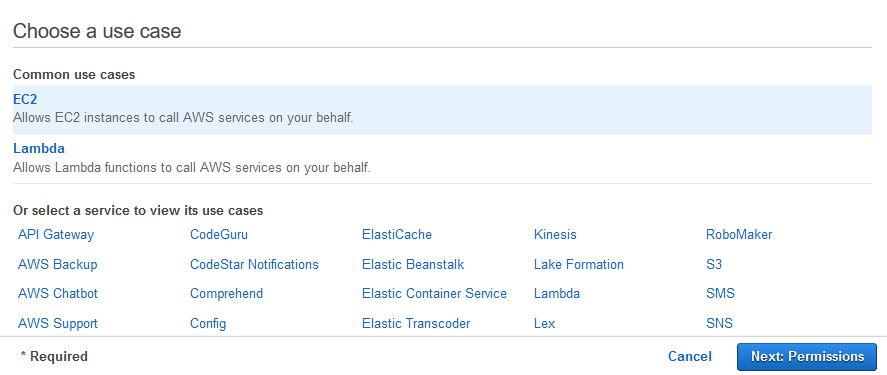
How To Add An EC2 Instance To AWS System Manager (SSM) Hello Everyone Welcome to CloudAffaire and this is Debjeet In the last blog post, we have discussed how to install AWS System Manager (SSM)Search and click on IAM from AWS navigation menu In the left navigation pane, click on Roles under the Access management drop down menu, and click Create role Select AWS service in Type of trusted entity, and EC2 in the common use case, then click Next PermissionsIf your instances are already connected to an instance profile that includes the AmazonSSMManagedInstanceCore AWS Managed Policy, the appropriate Session Manager permissions are already issued However, in specific instances, permissions may have to be changed to add session manager permissions to an instance profile

Securing Access To Emr Clusters Using Aws Systems Manager Noise
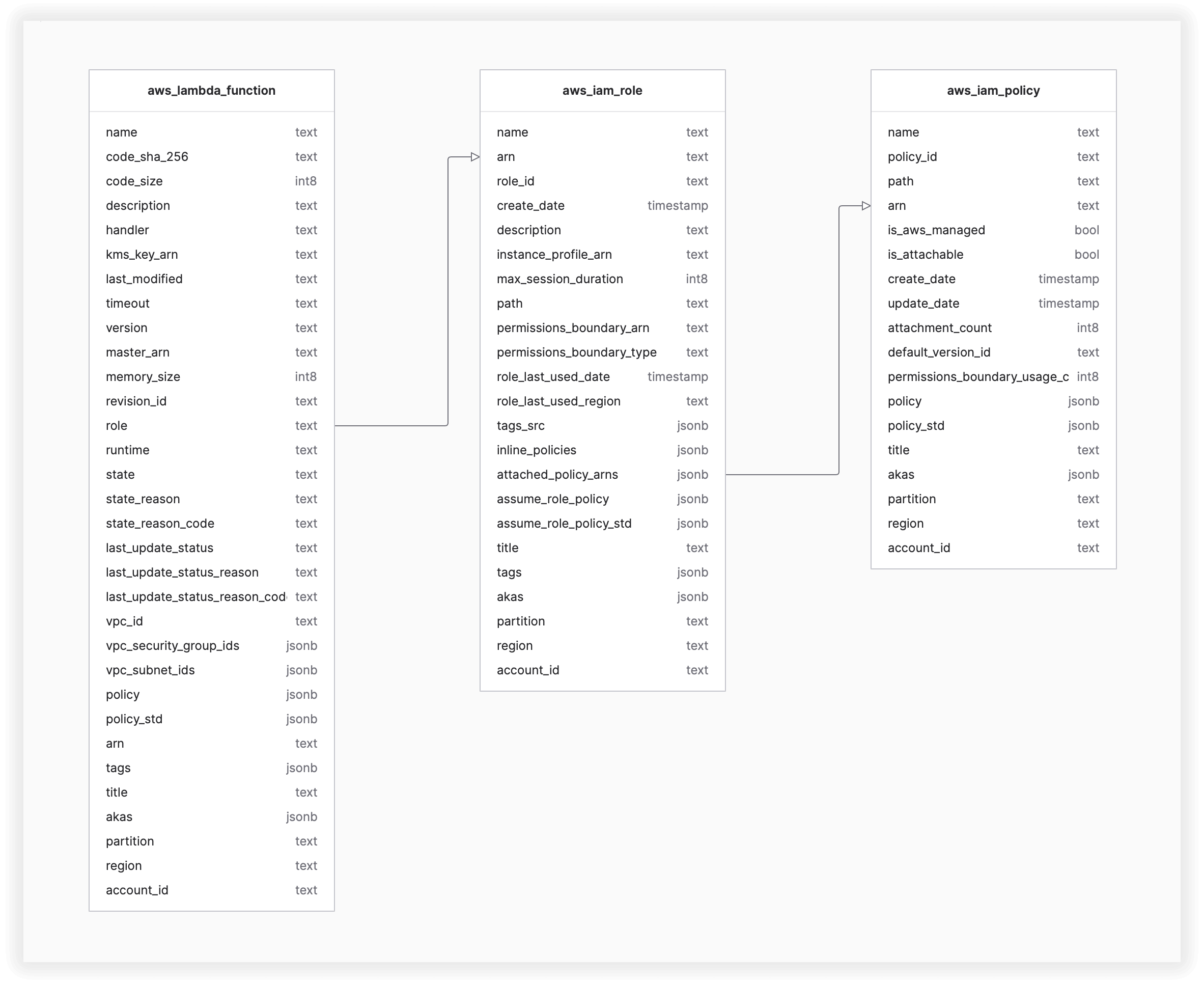
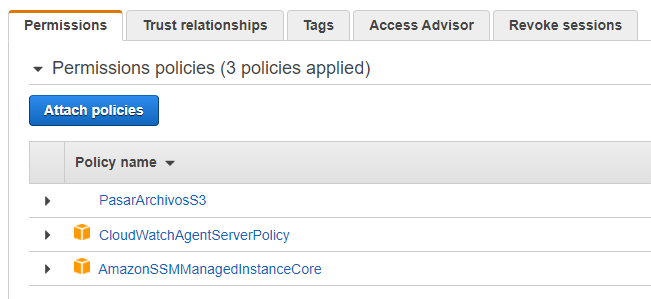
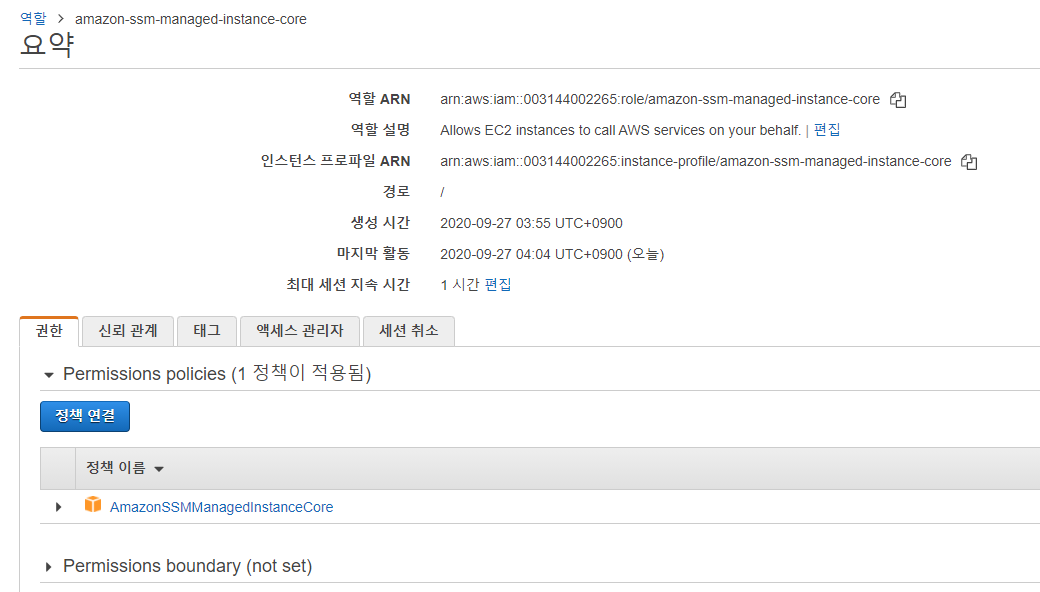
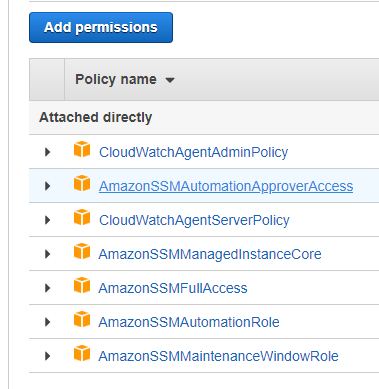
Amazonssmmanagedinstancecore permissions
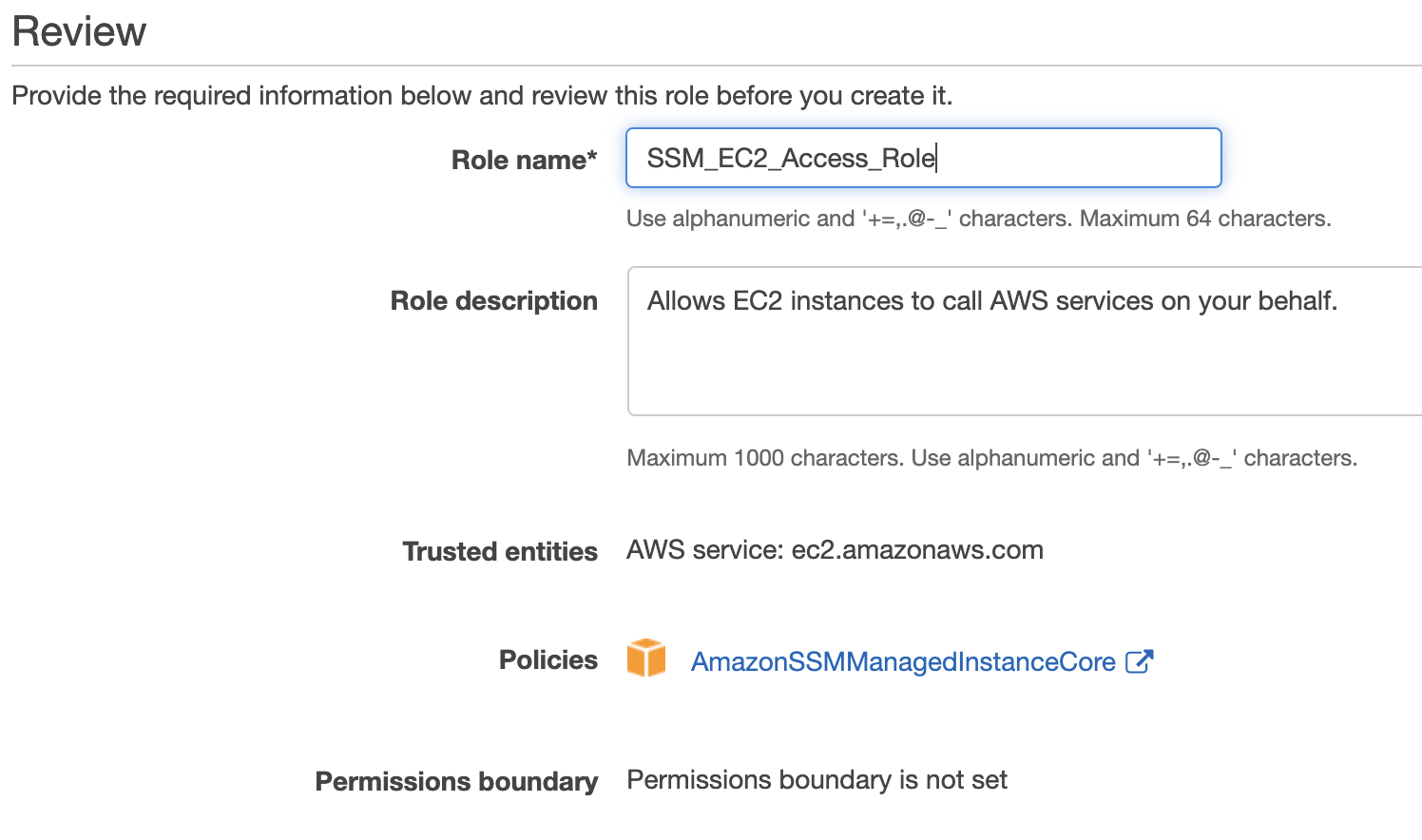
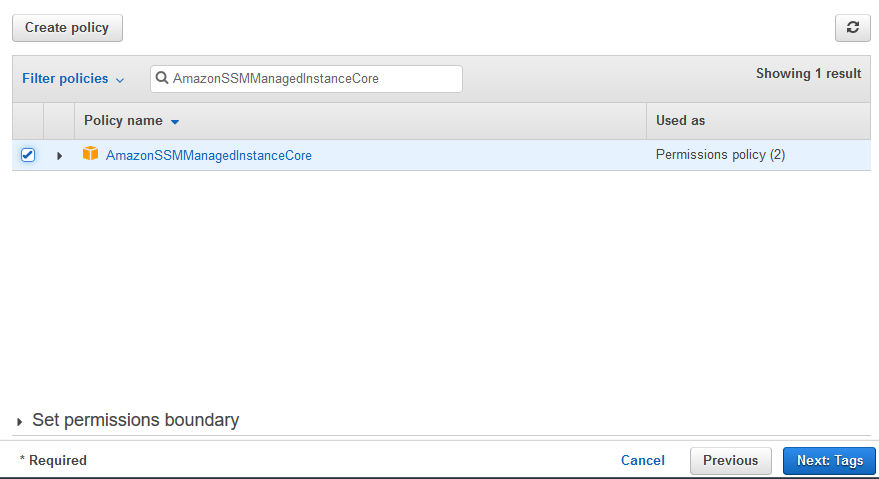
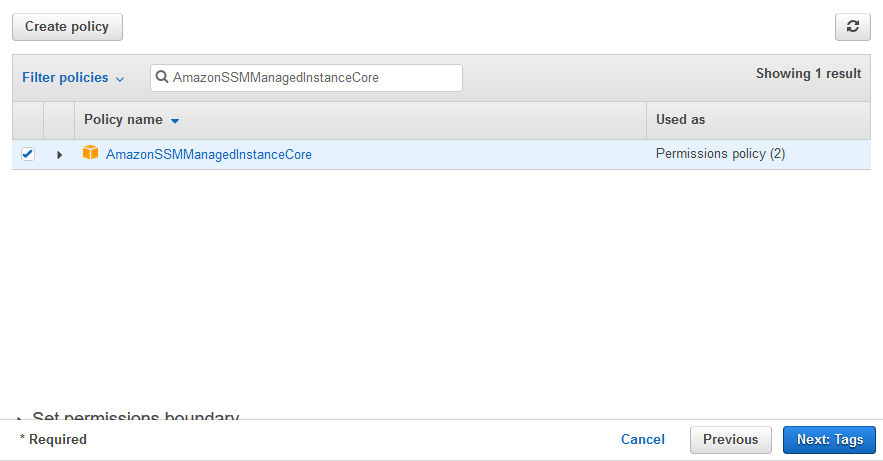
Amazonssmmanagedinstancecore permissions- then, click on ec2 and permissions click on AmazonSSMManagedInstanceCore policy skip the tags now, we c an see that there is a role name SSMInstancePrp Then click on create role now, go back to our ec2 instance follow the steps as below a)click on ec2 instance b)select actionsIn the Import managed policies window, add the "AmazonSSMManagedInstanceCore" policy Create a role and assign the policy Follow the instructions in Creating a role for an AWS service In the Attach permissions policies window, add the "AmazonSSMManagedInstanceCore" permission Create parameters



Aws Private Ec2 Instance Ssh Access By Stefan Poltl Medium
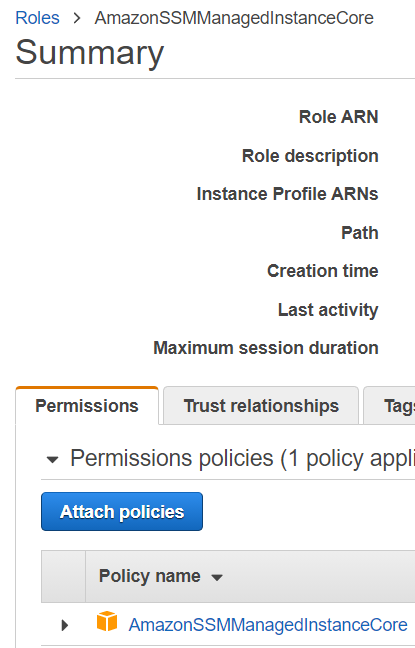
AmazonSSMManagedInstanceCore, enables an instance to use AWS Systems Manager service core functionality Depending on your operations plan, you might need permissions represented in one or more of the other three policies To view this policy in the console go to services, IAM, Access Management, Policies and search for th IntroductionSSM Agent Addon¶ This addon uses the Kubernetes DaemonSet resource type to install AWS Systems Manager Agent (SSM Agent) on all worker nodes, instead of installing it manually or replacing the Amazon Machine Image (AMI) for the nodesYou can grant CloudRanger permissions to use the Parameter Store values on script execution Note The AWSmanaged instance policy 'AmazonSSMManagedInstanceCore' contains the required permissions which allow the instance to use
User permission ADMINISTER BULK OPERATIONS is not supported on Linux at this time For more, I recommend reading the release notes for SQL Server 19 on Linux from Microsoft Summary I identified the requirements of my use case I created and configured a SQL 19 Server on an Amazon Linux AMI To make APIs calls to a Systems Manager endpoint, you must attach the AmazonSSMManagedInstanceCore permissions policy to the IAM role attached to your instance If you're using a custom IAM policy, confirm that your custom policy uses the permissions found under AmazonSSMManagedInstanceCore Procedure From the navigation pane, go to Protect > Virtualization The Virtual machines page appears On the Hypervisors tab, click Add hypervisor From the Select vendor list, select Amazon In Client name, type a descriptive name for the hypervisor To specify a region for the access nodes that you are adding to the hypervisor, from the
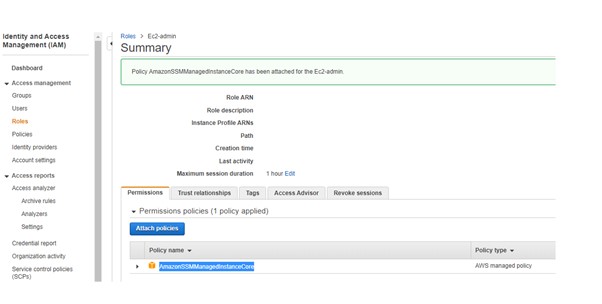
The issue was caused by incorrect permissions in the instance role used Changing policies in the role from AmazonSSMManagedInstanceCore to AmazonEC2RoleforSSM solved the issue Share Improve this answer Follow answered Jul 1 ' at 423 Marcin Marcin4 Create IAM Role You create IAM Role with AmazonSSMManagedInstanceCore Policy which is attached with the EC2 instances launched It makes the instances managed instances Goto the IAM Management console Click on the Roles menu in the left and then click on the Create role button On the next screen, select EC2 as the service and click on the Next Permissions button Under permissions, add "AmazonSSMManagedInstanceCore" Go to Systems Manager > Session Manager > Preferences > Edit Enable "Run As Support" and set the "Run As Defualt User" to be "ec2user" (or whatever the default user for your Elastic Beanstalk servers is)




Permissions Reference For Aws Iam Permissions Cloud



Aws Systems Manager Session Manager Bye Bye Bastion Hosts Pipetail Blog
To use Session Manager, the EC2 instance you want to connect to must include an IAM instance profile with Session Manager permissions This instance profile must have a trust relationship to Amazon EC2 and include the permissions granted by the managed AmazonSSMManagedInstanceCore policyAdding Session Manager permissions to an existing instance profile Sign in to the AWS Management Console and open the IAM console at https//consoleawsamazoncom/iam/ In the navigation pane, choose Roles Choose the name of the role to embed a policy in Choose the Permissions tab Choose Add Instead, you seem to be confused with the assume_role_policy (also known as a "trust policy", this controls what IAM principals are allowed to use the role such as other AWS services or different AWS accounts etc) of a role and the role's permissions policy for what the role is allowed to do (eg read and write to an S3 bucket)




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com




Backup And Recovery Of Sap Hana Database Directly To Aws S3 Bucket Using Aws Backint Agent Part I
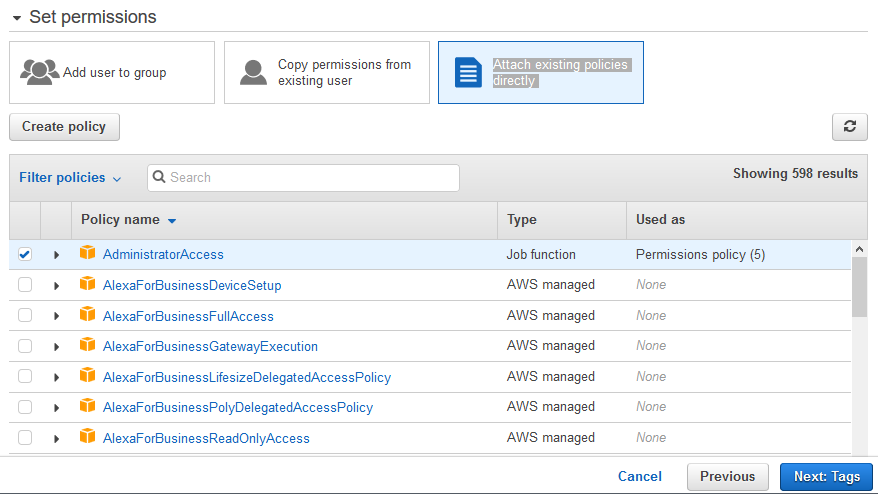
AWS documentation is simple but has many links which redirect users to various other documents to deploy application on AWS EC2 using code deploy and that seems to be confusing sometimes That is whyUnder "Common Use Cases" select "EC2 (Allows EC2 instances to call AWS services on your behalf)", then click Next Permissions In the policy search box enter "s3", then select the check box next to AmazonS3FullAccess Next, search for "ssm", then select the check box next to AmazonSSMManagedInstanceCoreA permission designed for admins, to intercept all local messages (ignoring the chatradius) This allows you to use urls in your chat messages Allows you to hide your country and city from people who have permission essentialsgeoipshow Shows the GeoIP location of a player, if the GeoIP module is installed




Terraform Aws Ec2 With Ssm Agent Installed




Securing Access To Emr Clusters Using Aws Systems Manager Noise
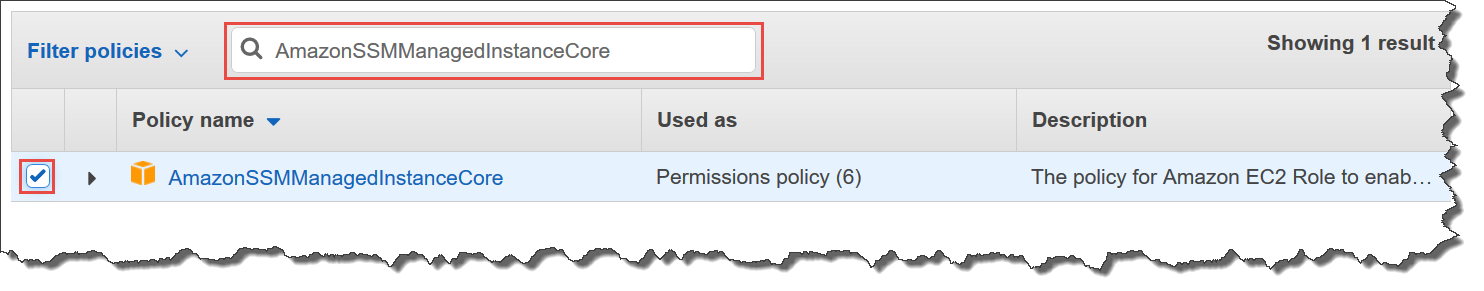
Core Permissions Attaches AmazonSSMManagedInstanceCore managed policy which is required to enable an instance to use Systems Manager service core functionality Access to Directory Services Attaches AmazonSSMDirectoryServiceAccess managed policy, required only if you plan to join EC2 instance for Windows Server to a Microsoft AD directory Access for Click on "NextPermissions" button in bottom right of page In Filter Policies search box, enter " AmazonSSMManagedInstanceCore " and select the policy by ticking CheckBox Follow the wizard and on last page enter the Role name (egThe nodes will have a node role attached to them with AmazonSSMManagedInstanceCore permissions;



How To Use Aws Sessions Manager To Remotely Connect To Your Forem Server Forem Creators And Builders



How To Securely Connect Ec2 Via Ssh With Aws Systems Manager By Ruslan Korniichuk Medium
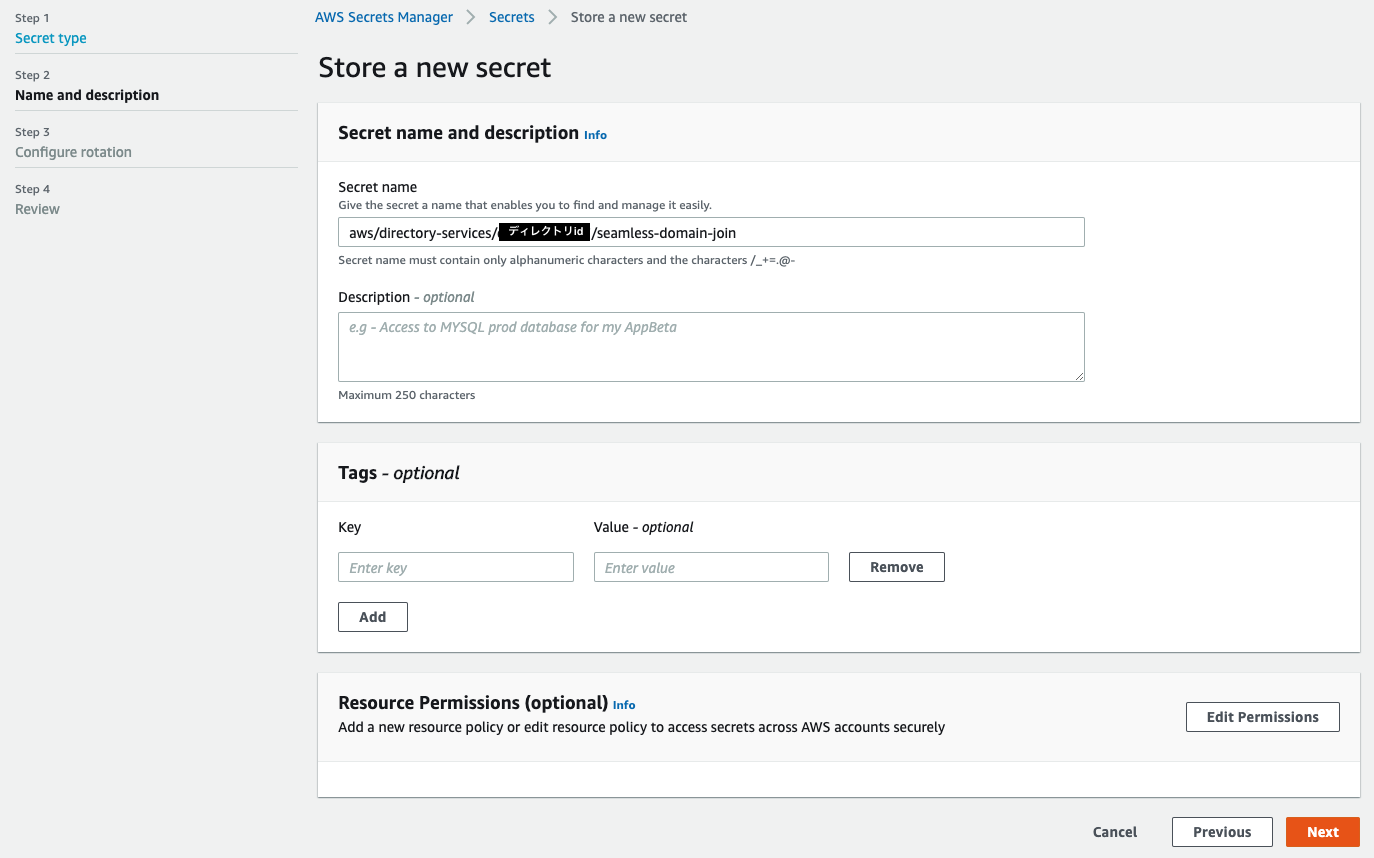
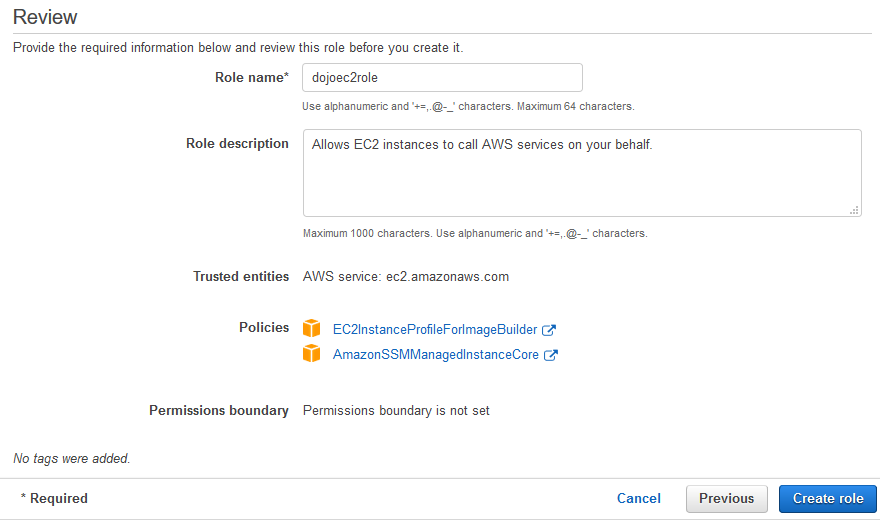
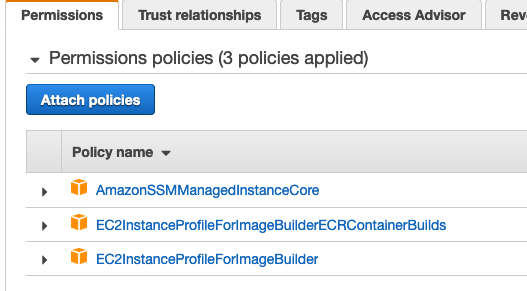
Today the team is unveiling a new feature which will enable a Linux EC2 instance, as it is launched, to connect to AWS Directory Service for Microsoft Active Directory seamlessly This complements the existing feature that allows Windows EC2 instances to seamlessly domain join as they are launched This capability will enable customers to move faster and improves theClick ' AWS service ' and choose ' EC2 ', click next On the Attach permissions policies, search for AmazonSSMManagedInstanceCore and select it Also search for EC2InstanceProfileForImageBuilder and select it as well Click Next, optionally tag your resource and click next againChoose Next Permissions In the Attach permissions policies page, search for AmazonSSMManagedInstanceCore, select the checkbox, and then choose Next s Optionally add tags for the IAM role and then choose Next Review In the Review section, enter a Role name, such as ManagedInstancesRole Accept the default in the Role description



Steampipe Parliament Steampipe Blog



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services
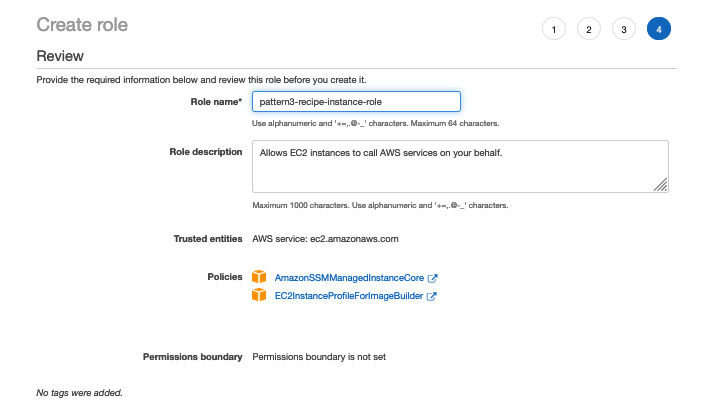
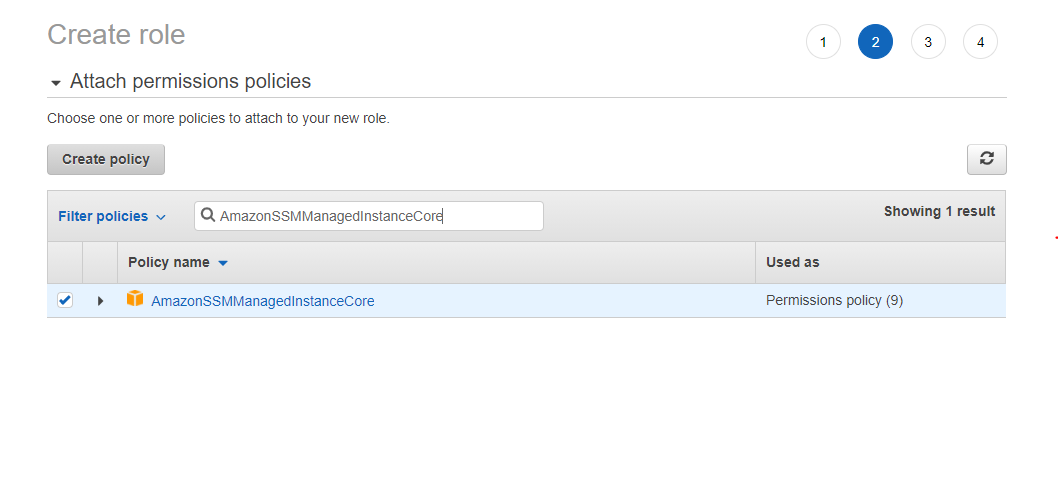
Keep the selected entity as "AWS Service", choose EC2 and click NextPermissions Search and select the predefined policy "AmazonSSMManagedInstanceCore", and click Nexts Click NextReview to continue Enter a role name (eg , role_for_ssm), and click Create role Make a note of the role nameThe EKS cluster will be created in the custom VPC created earlier Initiate the deployment with the following command, cdk deploy eksclusterstack01The AmazonSSMManagedInstanceCore Policy is required to be added to the EnablesEC2AccessSystemsManagerRole in AWS In the AWS Console, click IAM under Services In Access management, click Policies Use the Search to find AmazonSSMManagedInstanceCore and click the name to open the details Click Policy usage




Securing Access To Emr Clusters Using Aws Systems Manager Noise



はじめてのcloudwatch Agent導入 Ssm Centos サーバーワークスエンジニアブログ
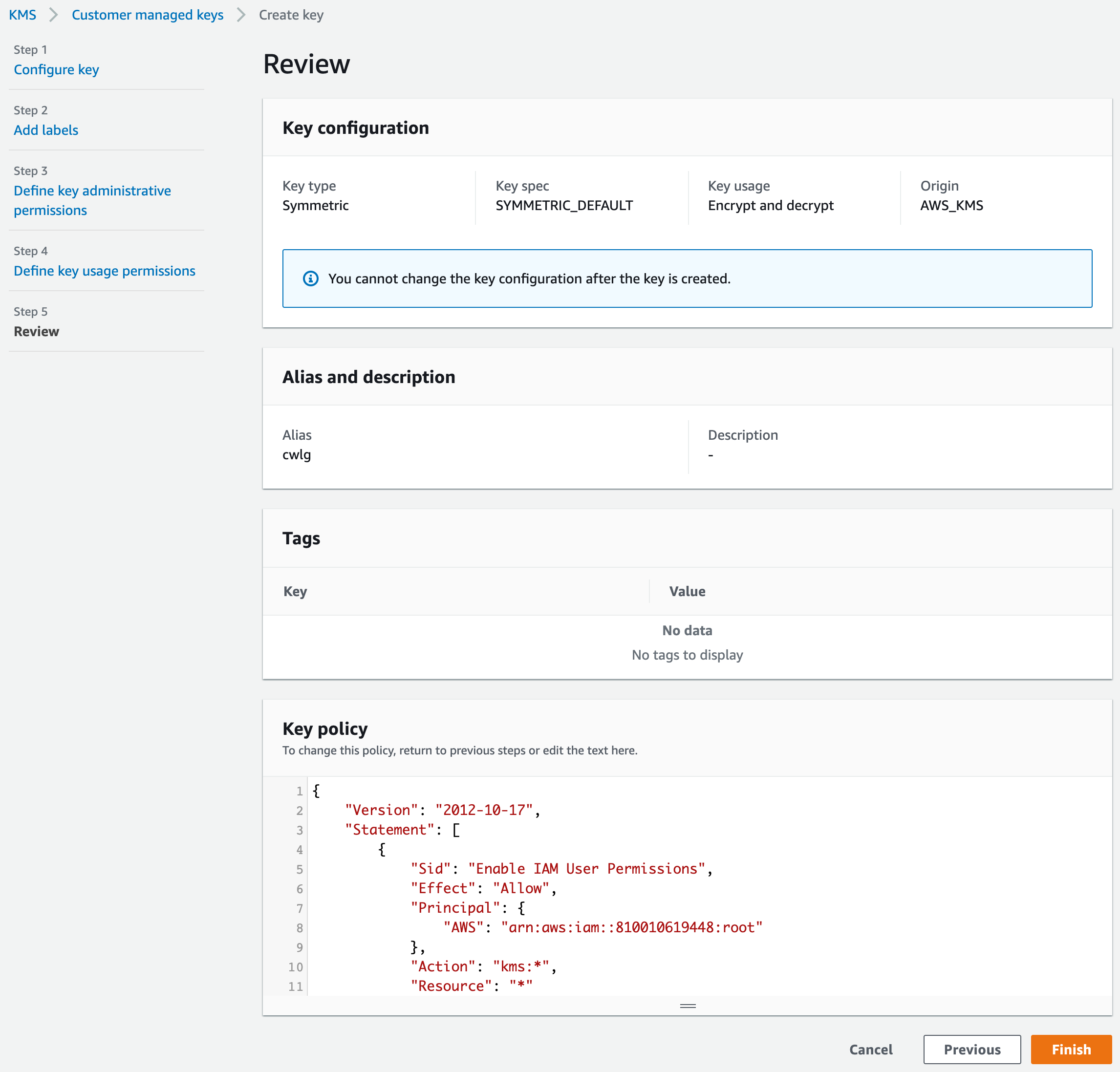
AmazonSSMManagedInstanceCore provides the minimum permissions necessary to use the Systems Manager service For more information about creating a role with these permissions, and for information about other permissions and policies you can assign to your IAM role, see Create an IAM instance profile for Systems Manager in the AWS Systems Manager User GuideThe AmazonSSMManagedInstanceCore Policy is required to be added to the EnablesEC2AccessSystemsManagerRole in AWS In the AWS Console, click IAM under Services In Access management, click Policies Use the Search to find AmazonSSMManagedInstanceCore and click the name to open the details Click Policy usageHowever, as a starting point, you can use one or more of the following policies to grant permission for Systems Manager to interact with your instances The first policy, AmazonSSMManagedInstanceCore, allows an instance to use AWS Systems Manager service core functionality Depending on your operations plan, you might need permissions represented



Seamlessly Join A Linux Ec2 Instance To Aws Managed Microsoft Ad




Advlab5 Building Hyper V On Aws Using Bare Metal Instance My Aws Workshop
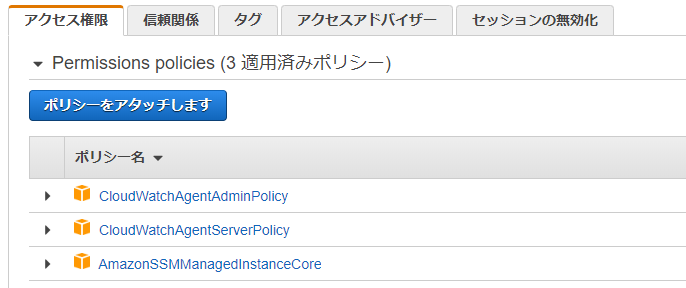
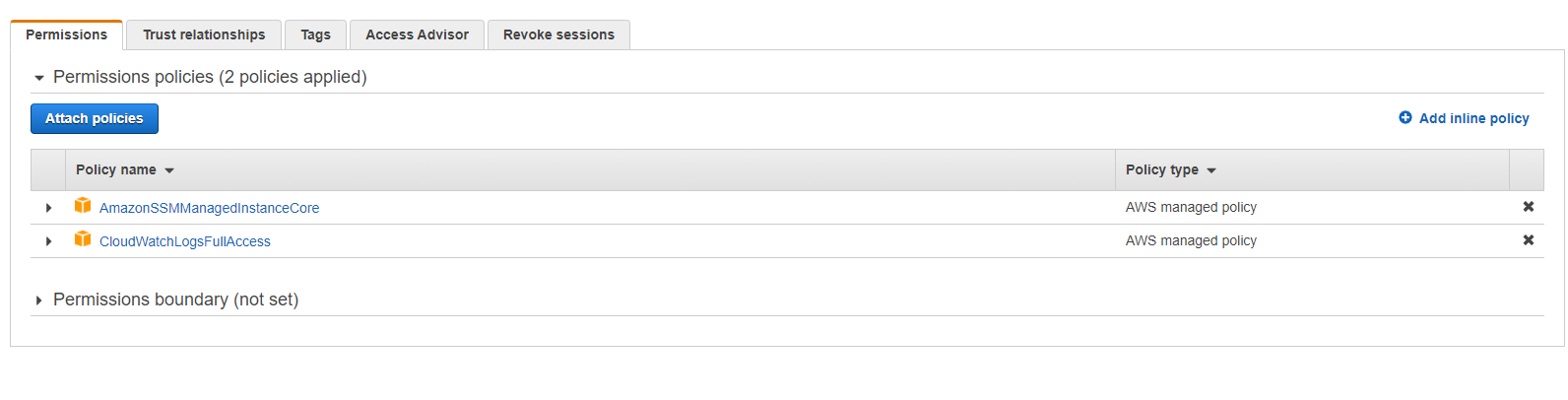
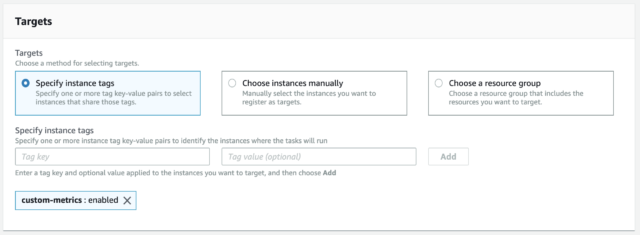
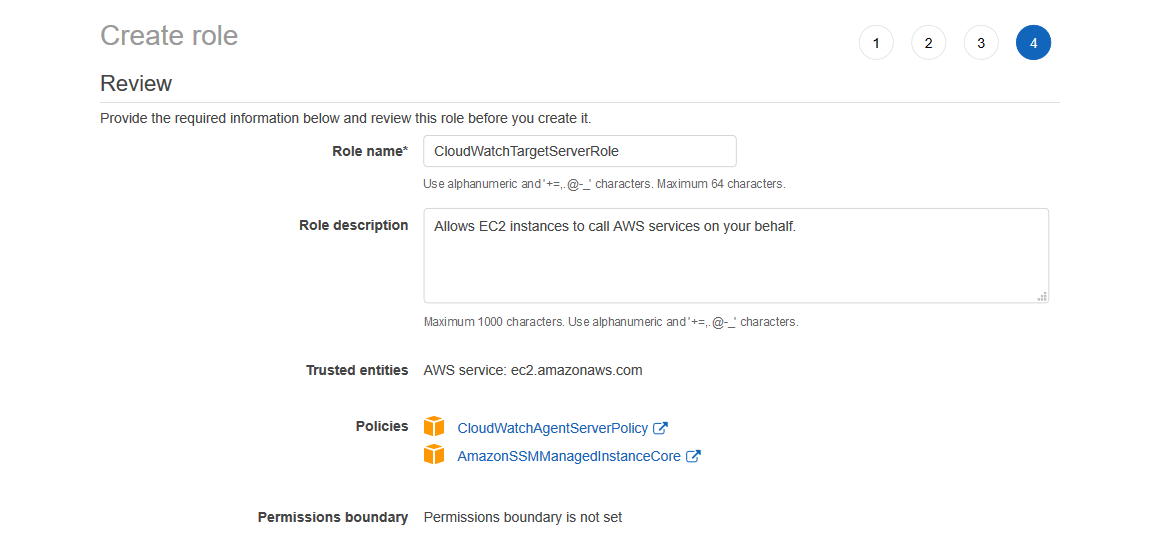
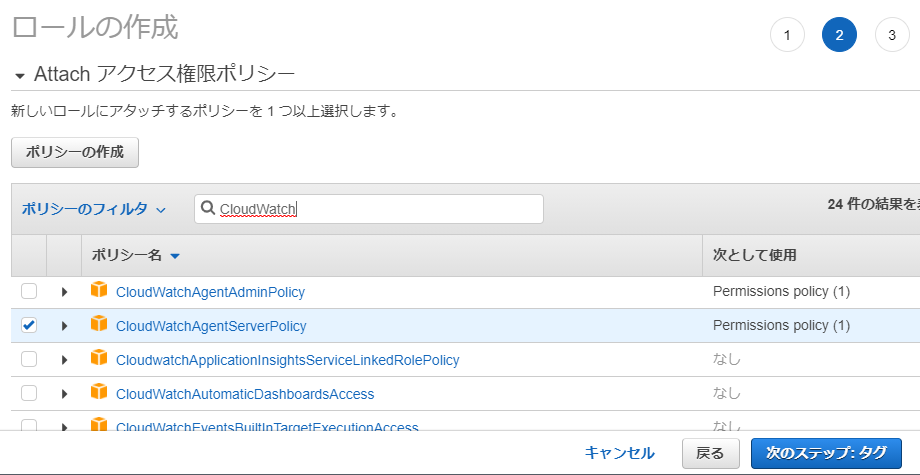
One of the most impressive features of PolyBase in SQL Server 19 is the ability to create scaleout groups, pairing it with its predecessors, Parallel Data Warehouse (PDW) and Analytics Platform Choose EC2 as the Service that will use this role and then go to Permissions Select the policies ' CloudWatchAgentAdminPolicy ' and ' AmazonSSMManagedInstanceCore ' Enter the role name ' CloudWatchAdminServerRole ' and the description, then Create Role As for the Target Server (s) Role, repeat steps 1 through 3;Click the NextPermissions button Attach Policy Permissions In the filter policy search box, type ssm Check the box next to AmazonSSMManagedInstanceCore from the policy names Click the Nexts button At the next screen, click the NextReview button At the next screen, give the role a Role name such as VPC64EC2role Click the Create



Nxsabgggjqodpm




How To Install Aws Ssm Agent On Redhat Rhel Decodingdevops
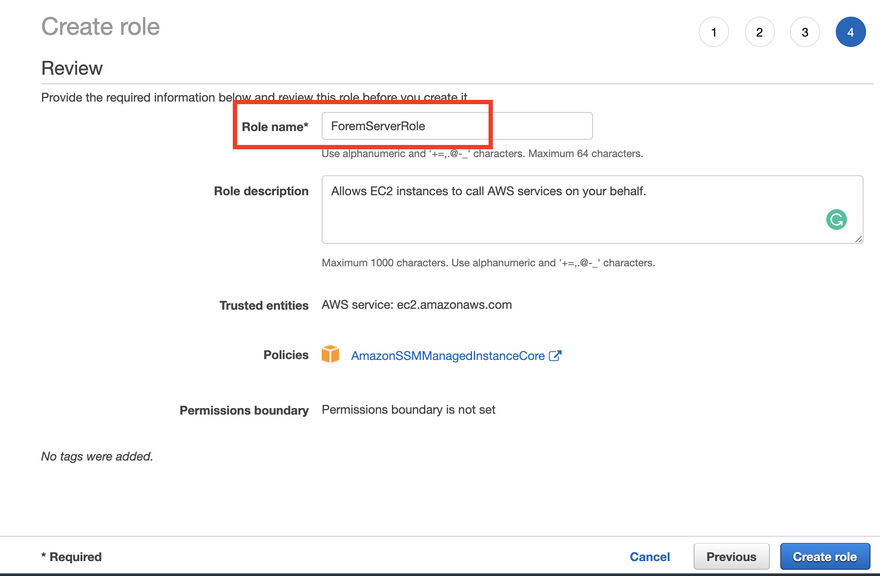
IAM Role To enable automatic scaling and backups on the VSA access node, select the IAM role that has both the AmazonSSMManagedInstanceCore managed policy and the amazon_permission_backup_restorejson file attached In the Import managed policies window, add the "AmazonSSMManagedInstanceCore" policy Create a role and assign the policy Follow the instructions in Creating a role for an AWS service In the Attach permissions policies window, add the "AmazonSSMManagedInstanceCore" permission Create parameters For permissions we want AmazonSSMManagedInstanceCore so type in Core and select it, proceed to tags and then proceed to review Name your Role, I recommend something like ForemServer and create the role Attach IAM Role to EC2 server Now that we have the role lets go back to our EC2 instance
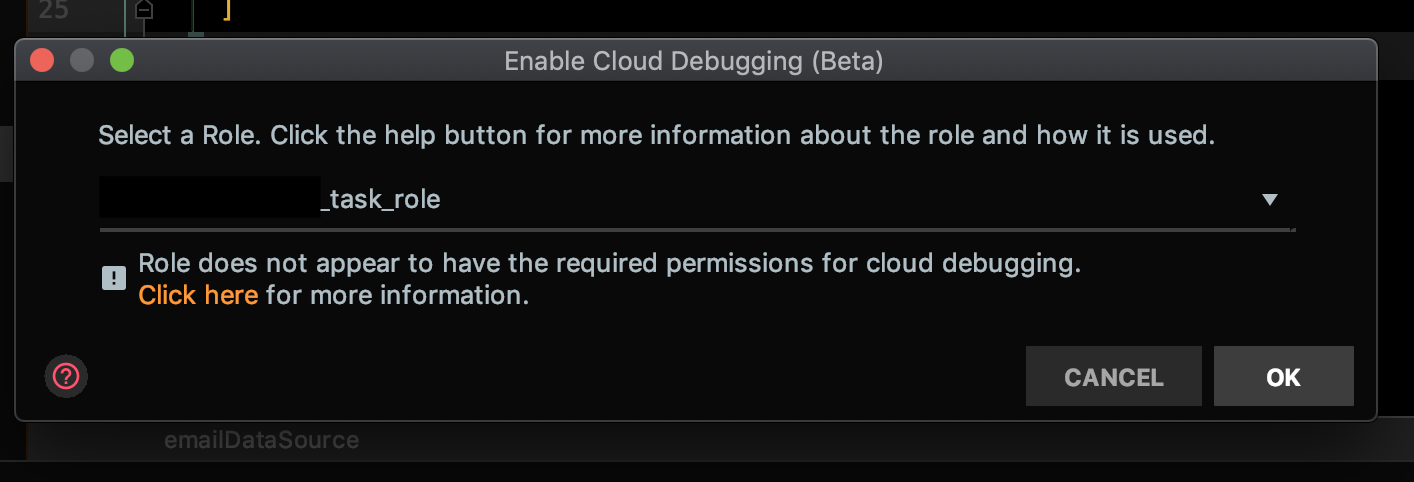



Unclear What Aws Role Permissions I Need For Aws Cloud Debugging With Webstorm Plugin Issue 1461 Aws Aws Toolkit Jetbrains Github



Aws Secure Access Infrastructure Identity Workshop 02 Using Aws Systems Manager Session Manager Md At Master Aws Samples Aws Secure Access Infrastructure Identity Workshop Github
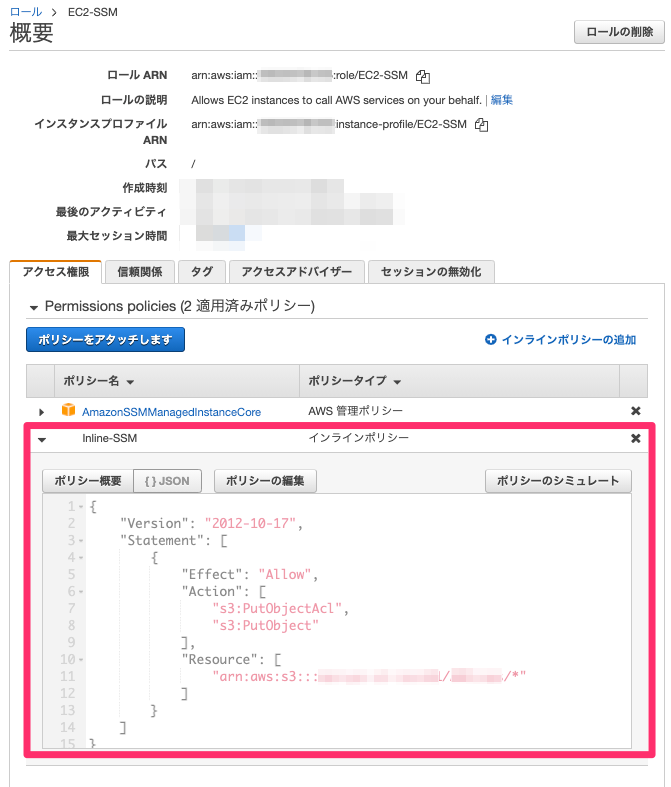
Permissions Policy AmazonSSMManagedInstanceCore attached in IAM Role of EC2 instance To install AWSDistroOTelCollector package using AWS Systems Manager Distributor Based on your preferences, prepare AWS Distro for OpenTelemetry Collector YAML configuration file according to AWS OTel Collector Configuration To download the JSON file from your browser, see amazon_restricted_role_permissionsjson Use default security group To use the default security group, move the toggle key to the right If you select this option, the Commvault software assigns the default security group that is defined within your VPC, instead of a specific security group for



Ssh Logging And Session Management Using Aws Ssm Toptal




Microsoft Sccm Admins Get Started With Aws Systems Manager Patch Manager Aws Management Governance Blog




Applying Managed Instance Policy Best Practices Aws Management Governance Blog




Aws Private Ec2 Instance Ssh Access By Stefan Poltl Medium



How To Achieve A Secure Connection To Ec2 Virtual Servers With Session Manager Without The Need Of Encryption Keys Financial Solutions
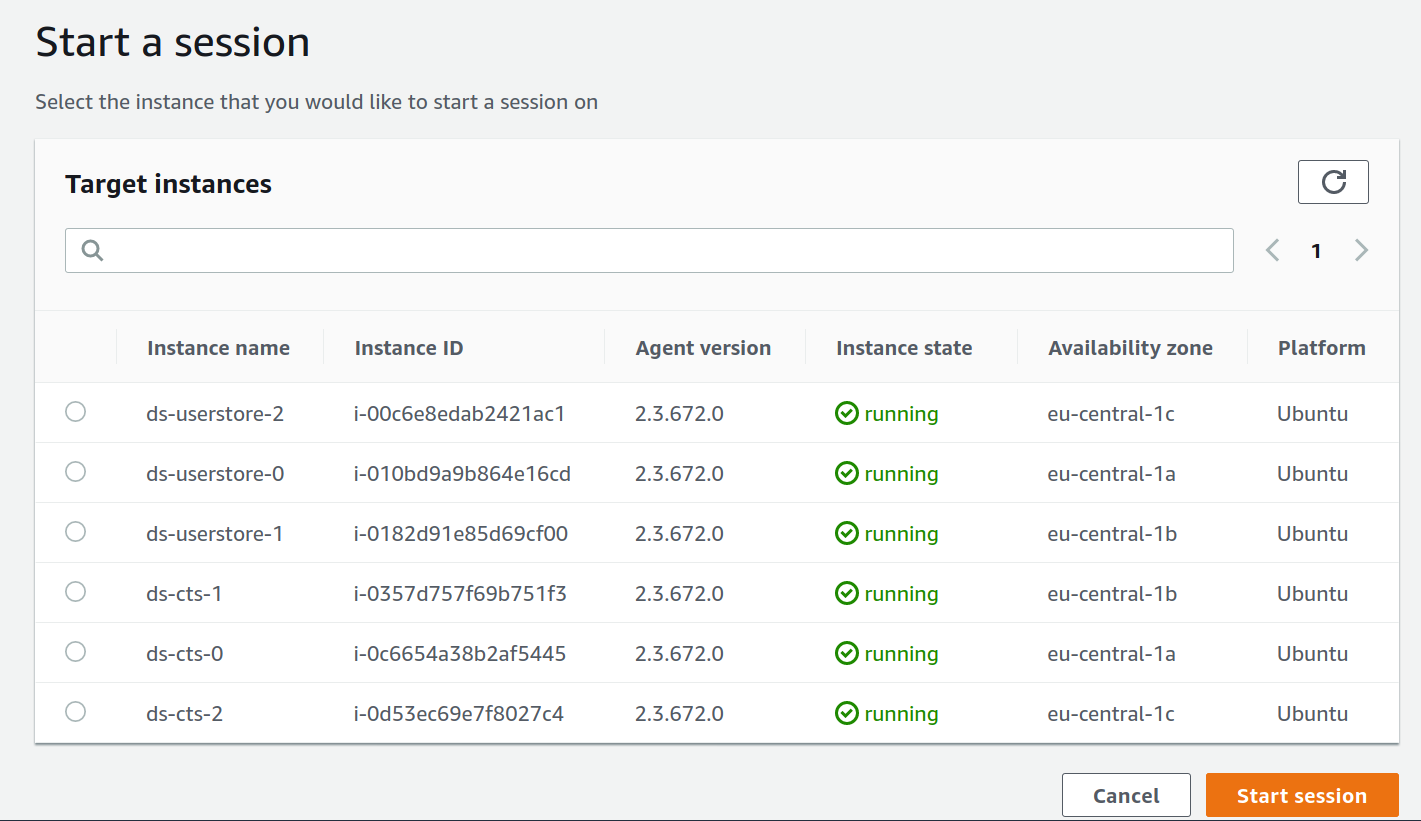



Aws Systems Manager Session Manager Bye Bye Bastion Hosts Pipetail Blog




Step 3 Administering Ad My Aws Workshop




Managing Your Instance Sessions Cmd Solutions Simplify Complexity
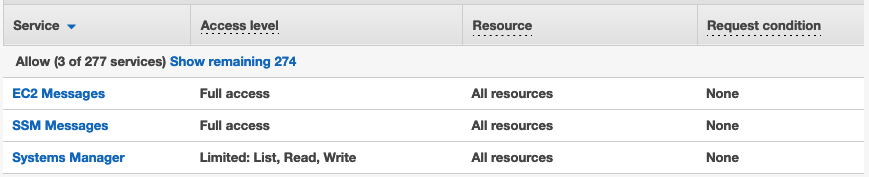



Still Using Ec2 Key Pairs Switch To Session Manager Now Qloudx




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com
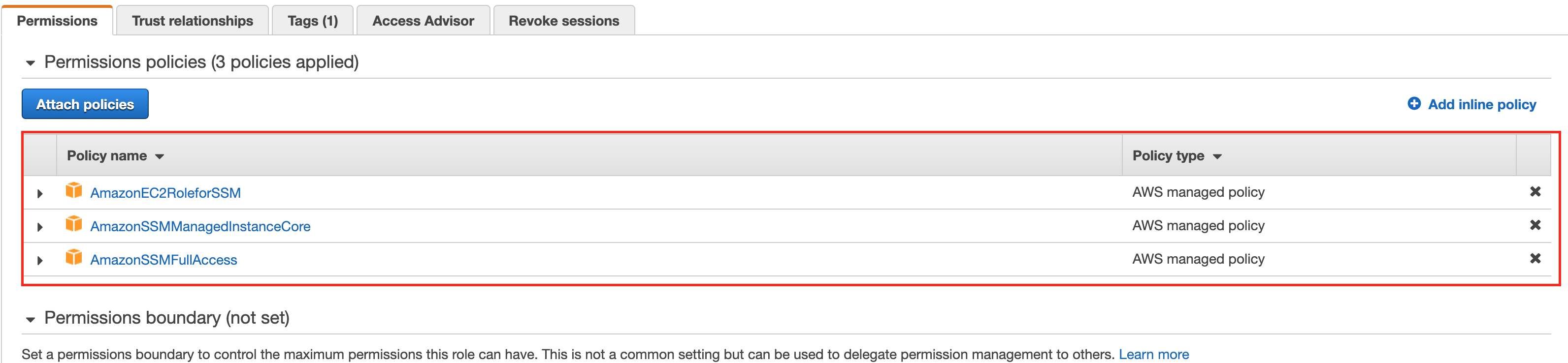



How To Provision Aws Ec2 In Private Subnet By Using Ssm And Ansible Dynamic Inventory Ru Rocker




How To Secure Your Instance Metadata Service On Aws Using Aws Systems Manager Run Commands Cevo




Directoryservice Admin Guide Pdf Active Directory Amazon Web Services




新ポリシー Amazonssmmanagedinstancecore がサポートされました Developersio
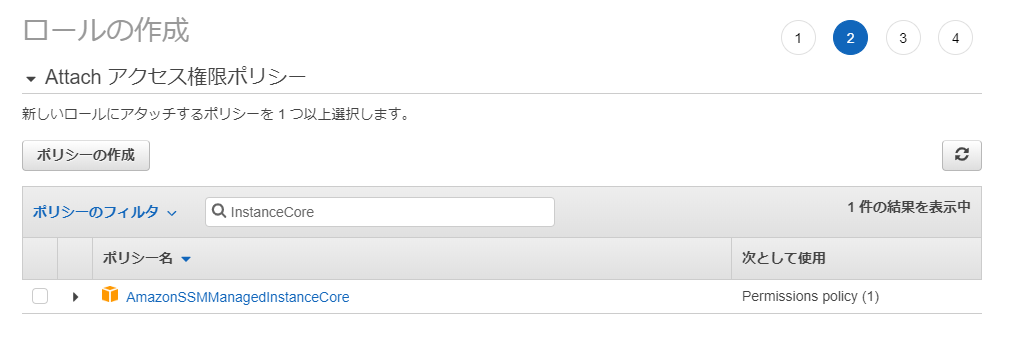



Session Manager を使用したec2へのコマンド接続 Fu3ak1 S Tech Days



Aws Systems Manager Compliance Aws Devops Week



How To Achieve A Secure Connection To Ec2 Virtual Servers With Session Manager Without The Need Of Encryption Keys Financial Solutions




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com
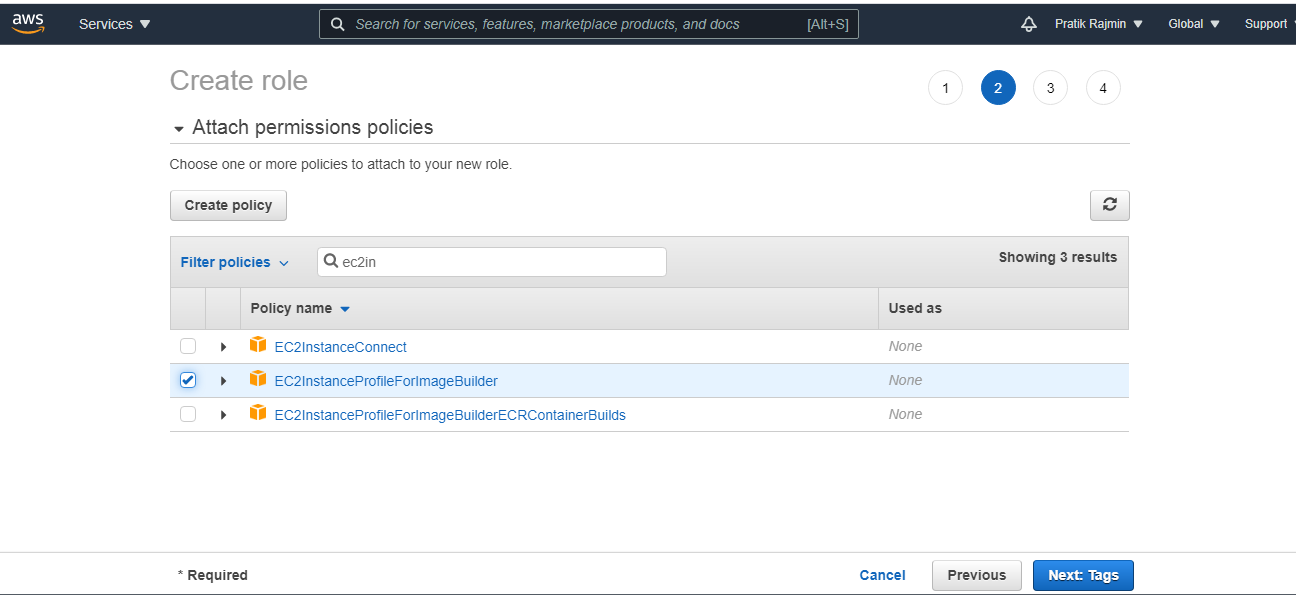



Image Creation With Ec2 Image Builder Eternal Blog



Deploy The Ami Builder Pipeline Aws Well Architected Labs



Still Using Ec2 Key Pairs Switch To Session Manager Now Qloudx



Ssh Logging And Session Management Using Aws Ssm Toptal




Step 3 Administering Ad My Aws Workshop



How To Achieve A Secure Connection To Ec2 Virtual Servers With Session Manager Without The Need Of Encryption Keys Financial Solutions



Still Using Ec2 Key Pairs Switch To Session Manager Now Qloudx



Aws Session Manager Connect To Ec2 Instance 隔叶黄莺yanbin Blog 软件编程实践




Applying Managed Instance Policy Best Practices Aws Management Governance Blog




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Stack Over Cloud



Introduction To Aws Systems Manager



Credentials Are Not Retrieved From Aws Imdsv2 When Running On Ec2 Issue 2840 Fluent Fluent Bit Github




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise




Using Aws Systems Manager Run Command To Submit Spark Hadoop Jobs On Amazon Emr Aws Management Governance Blog



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio



Securely Access Windows Ec2 Instances Using Session Manager Fit Devops




One Stop It Service Provider Build Stig Compliant Amazon Machine Images Using Amazon Ec2 Image Builder Rapidly




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise




Task 7 Create Instance Iam Role Ipv6 Workshop




Securing Access To Emr Clusters Using Aws Systems Manager Noise



2




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com



Export Ec2 Logs To Cloudwatch I Was Recently Tasked With Finding A By Omar Dulaimi Medium




How To Secure Your Instance Metadata Service On Aws Using Aws Systems Manager Run Commands Cevo



Why Does The Ssm Run Command Fail On My Ec2 Windows Server Developersio



Github Mjuettner Aws Ssm Ec2ic Demo This Demonstration Will Show Two Examples Of How To Configure Your Aws Resources To Allow Secure Access To Your Ec2 Instances




Applying Managed Instance Policy Best Practices Aws Management Governance Blog



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services



Aws Link Memory Usage Of Ubuntu Ec2 Instance To Cloudwatch




Applying Managed Instance Policy Best Practices Aws Management Governance Blog




Building Amis Packer And Image Builder Kubes Clouds




Lpionxc Pqqvum




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Noise



Connect To Windows Ec2 Instances In A Private Subnet On Aws By System Manager Instead Of Bastion By Leo Lee Ntt Data Cloud Medium
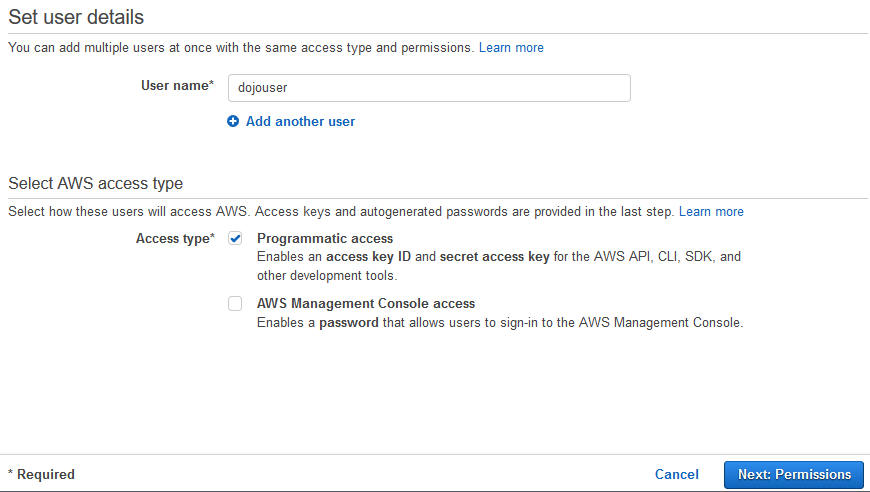



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services
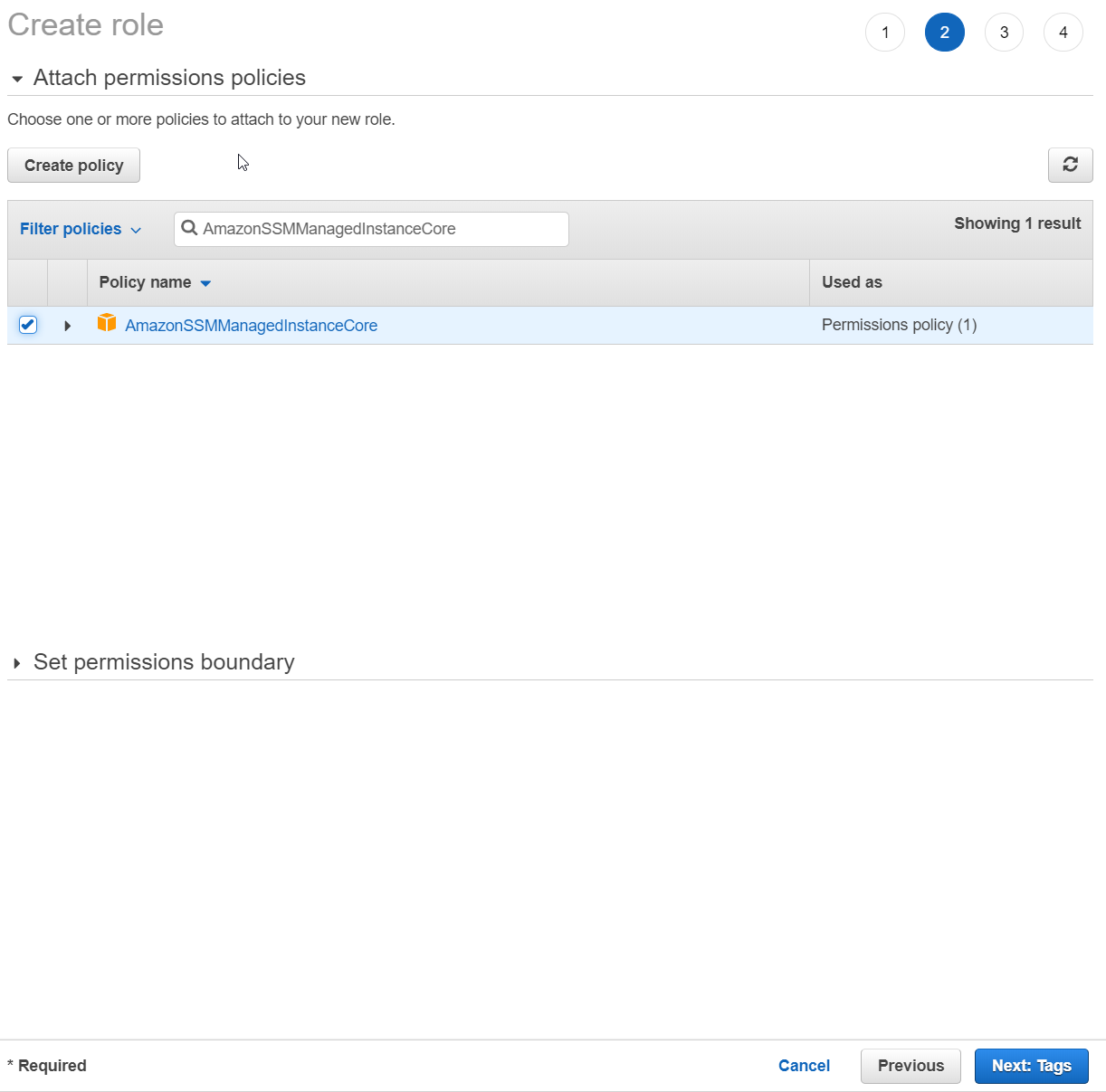



How To Reset Password To An Ec2 Windows Instance By Using System Manager Appuals Com
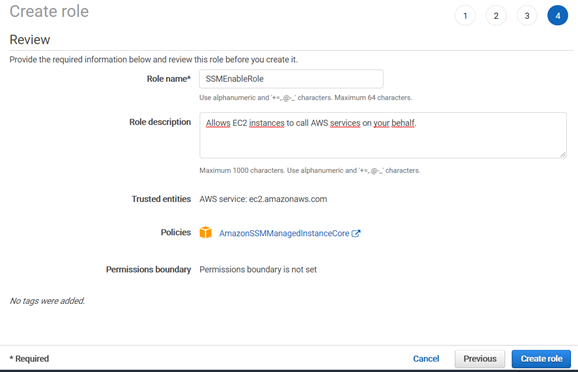



Bigfix Client Installation On Amazon Web Services A Practical Guide Blog




Task 7 Create Instance Iam Role Ipv6 Workshop




Hosting Asp Net Apps On Aws Part 14 Monitoring With Cloudwatch Joeplaa Com
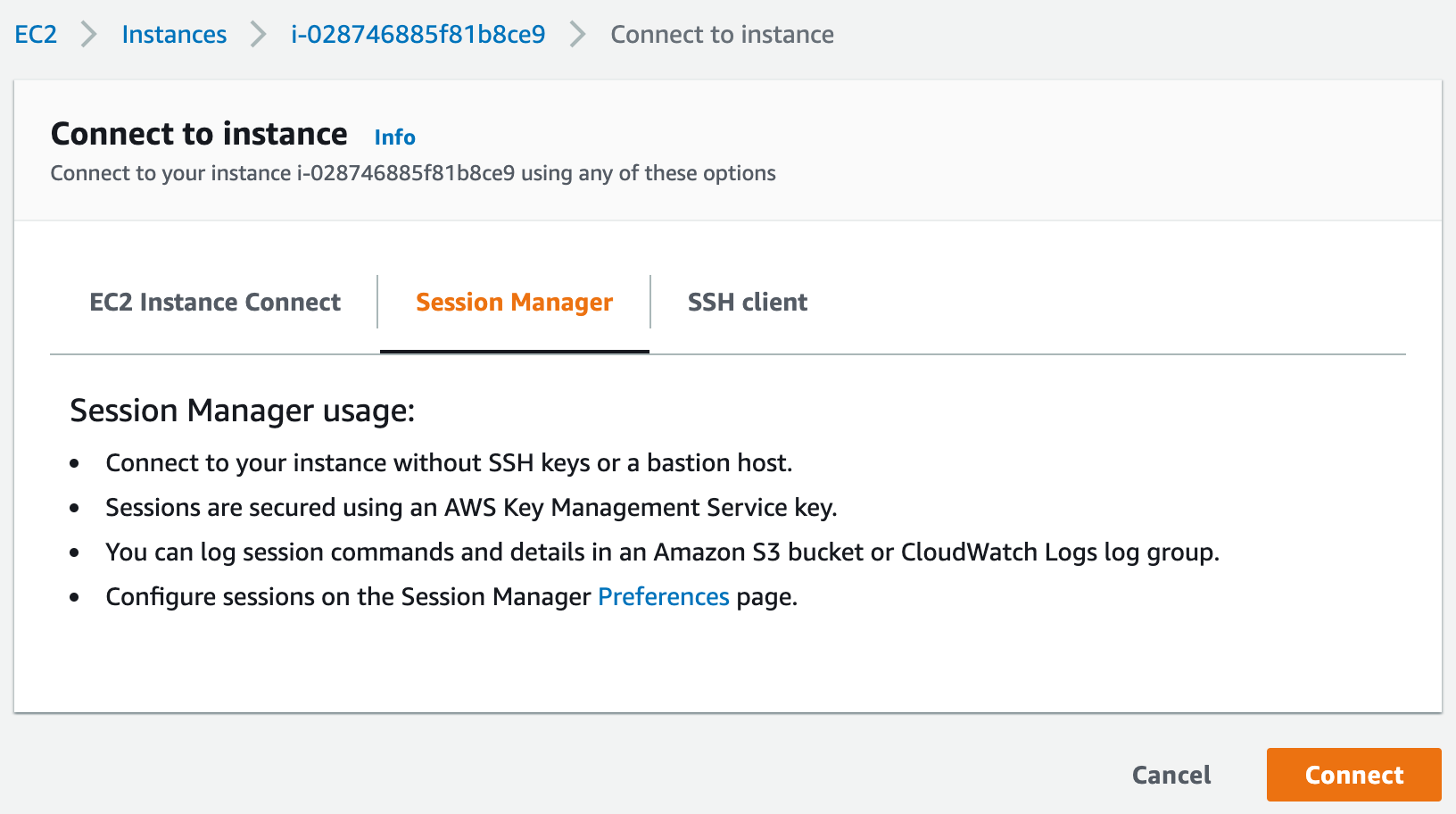



Aws Session Manager Connect To Ec2 Instance 隔叶黄莺yanbin Blog 软件编程实践



Aws Ssm으로 Private Subnet Ec2 접근하기



Step 4 Create An Iam Instance Profile For Systems Manager Aws Systems Manager




How To Secure Your Instance Metadata Service On Aws Using Aws Systems Manager Run Commands Cevo




1 2 Ec2 Instance Profile Ec2 Image Builder Workshop



Ssmのログを別awsアカウントs3に送る方法 Developersio




Who Holds The Keys To The Kingdom Part 1 Of 2 Ermetic



Aws Automation



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services



100 Days Of Devops Day 37 Automate The Process Of Ami Creation Using System Manager Maintenance Windows By Prashant Lakhera Medium



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services



Ami Management Eks Best Practices Guides
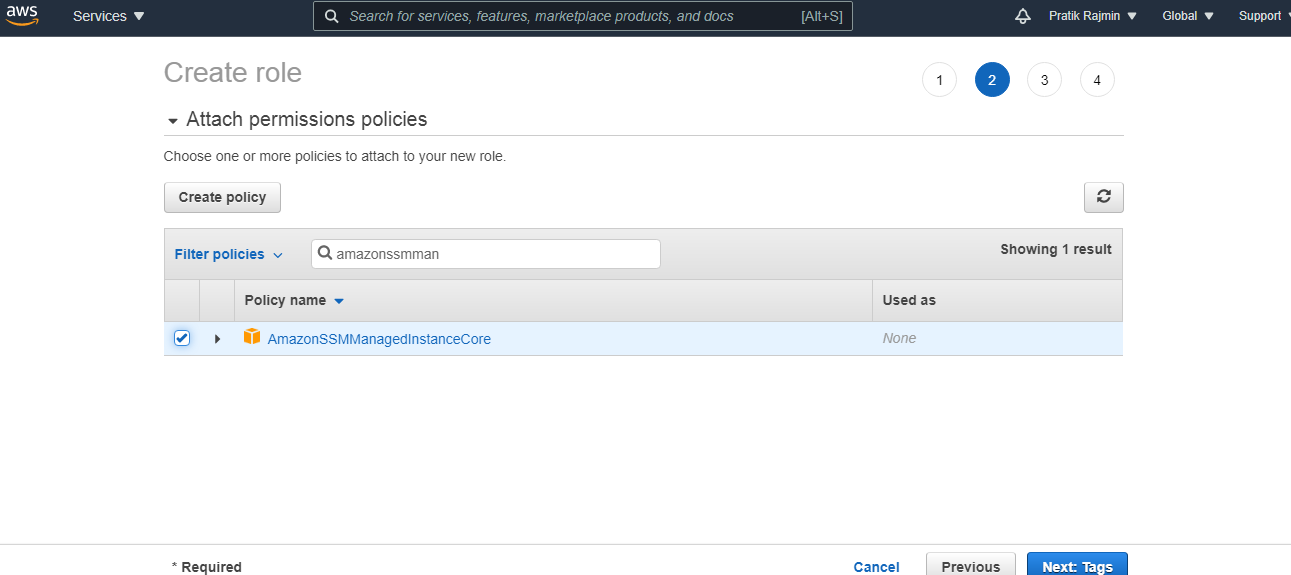



Image Creation With Ec2 Image Builder Eternal Blog




Seamlessly Join A Linux Instance To Aws Directory Service For Microsoft Active Directory Stack Over Cloud



2 Evaluate Session Manager Configuration Aws Cloud Security Virtual Event



Aws Dojo Free Workshops Exercises And Tutorials For Amazon Web Services



Aws Automation



Connect Ec2 Instance Using Aws Session Manager



Securely Access Ec2 Instance Using Systems Manager Without Ssh Keys Dataevolve Blogs



Ubuntu 18 04 On Premise Issue 247 Aws Amazon Ssm Agent Github



How To Install Aws Ssm Agent On Centos 8 Centos 7 Computingforgeeks



Going Bastion Less Accessing Private Ec2 Instance With Session Manager By Daniel Da Costa Towards Data Science




Improve Monitoring Of Aws Systems Manager Agent Cloudpro Exam Prep



New Aws Systems Manager Session Manager For Shell Access To Ec2 Instances Aws News Blog
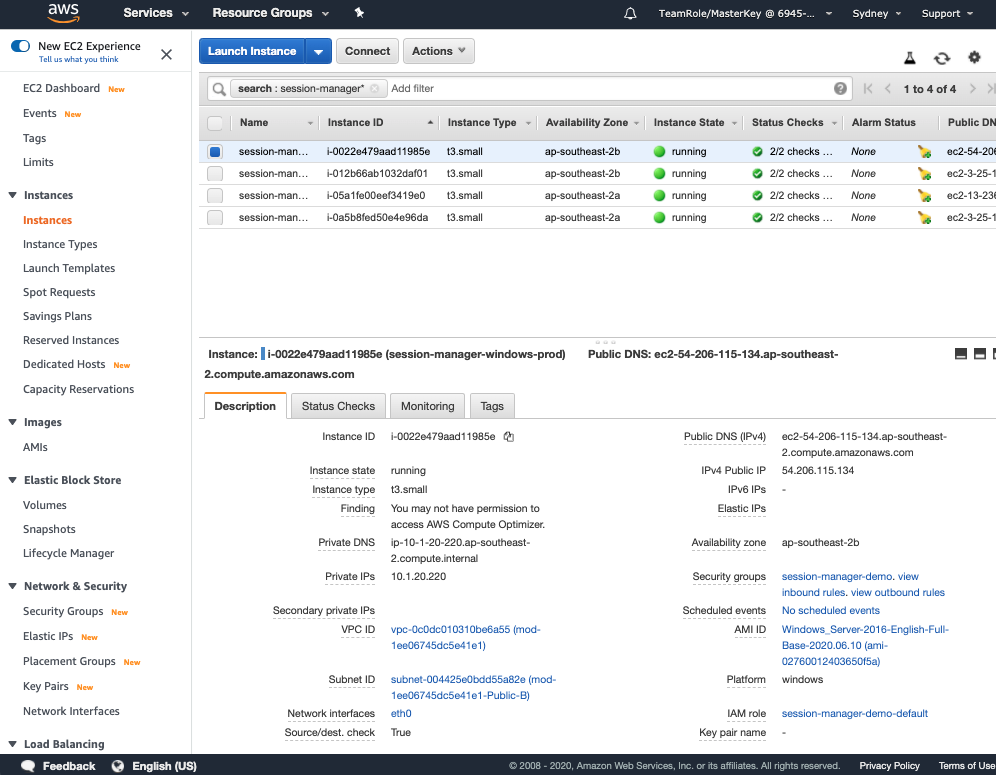



2 Evaluate Session Manager Configuration Aws Cloud Security Virtual Event



0 件のコメント:
コメントを投稿